Check 29+ pages active directory in networks segmented by firewalls answer in Doc format. For more information about configuring firewalls for use with AD DS see Active Directory in Networks Segmented by Firewalls. 13This paper also provides detailed procedures for configuring IPSec policies to protect Active Directory traffic between domain controllers on opposite sides of a firewall and recommended practices for managing IPSec policies that are assigned to domain controllers. Opening above ports in Firewall between client computers and domain controllers or between domain controllers will enable Active Directory to function properly. Read also segmented and active directory in networks segmented by firewalls For information about managing replication through firewalls see the article Active Directory in Networks Segmented by Firewalls.
21There is an excellent Microsoft whitepaper which addresses this topic. 1 domain controllers separated.
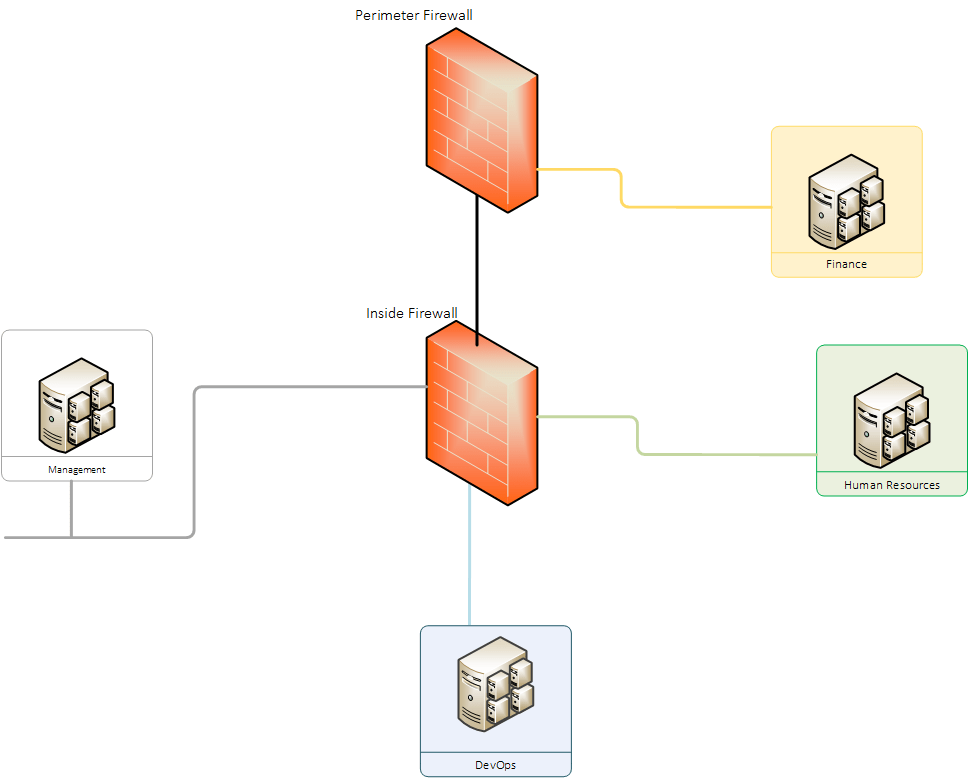
Digital System Provides Solution For Solutions Segmentation Understanding 24Active Directory in Networks Segmented by Firewalls Microsoft Corporation Published.
| Topic: Microsoft Active Directory service domain controllers are increasingly being deployed on networks segmented by firewalls. Digital System Provides Solution For Solutions Segmentation Understanding Active Directory In Networks Segmented By Firewalls |
| Content: Analysis |
| File Format: PDF |
| File size: 1.4mb |
| Number of Pages: 55+ pages |
| Publication Date: May 2021 |
| Open Digital System Provides Solution For Solutions Segmentation Understanding |
 |
Three common scenarios are 1 domain controllers separated from clients in a DMZ 2 domain controllers in a DMZ separated from other domain controllers on the network and 3 networks divided into segments each containing clients and domain controllers.

If the use of Kerberos V5 authentication is not possible because two-way trusts across forests cannot be established as in some large enterprise environments you can use a public key infrastructure PKI and digital certificates to establish IPsec-trusted. Three common scenarios are. 7You also need to open the firewall enough to allow Active Directory traffic to pass through. 8The organization wanted to put some firewalls in place between the networks located in each country while still allowing Active Directory to function properly with the idea that if the network in Country X was compromised the damage could be contained and Active Directory in the remaining countries would remain unaffected. Active Directory Networking security Windows-Microsoft. 26Active Directory in Networks Segmented by Firewalls October 26 2004 Edit Domain Controllers are increasingly being deployed on networks segmented by firewalls a common scenarios is a DC separated from clients in a perimeter network also known as DMZ demilitarized zone and screened subnet.

Work Infrastructure Map Work Infrastructure Working Map This scenario uses many of the operational building blocks described in Operational Building Blocks earlier in this paper.
| Topic: The firewall must not allow direct access from the Internet towards this Internal network. Work Infrastructure Map Work Infrastructure Working Map Active Directory In Networks Segmented By Firewalls |
| Content: Learning Guide |
| File Format: Google Sheet |
| File size: 1.5mb |
| Number of Pages: 35+ pages |
| Publication Date: February 2017 |
| Open Work Infrastructure Map Work Infrastructure Working Map |
 |

A Local Area Work Lan That Interconnects Puters In A Limited Area In This Example A School You Can Modify The D Local Area Work Diagram Working 21Deploying Active Directory in such networks requires additional configuration of the domain controllers and the firewalls to enable user and resource authentication and Active Directory replication across the firewalls.
| Topic: Use a resource forest and reconfigure the firewall for service isolation with limited connectivity. A Local Area Work Lan That Interconnects Puters In A Limited Area In This Example A School You Can Modify The D Local Area Work Diagram Working Active Directory In Networks Segmented By Firewalls |
| Content: Explanation |
| File Format: Google Sheet |
| File size: 725kb |
| Number of Pages: 10+ pages |
| Publication Date: January 2018 |
| Open A Local Area Work Lan That Interconnects Puters In A Limited Area In This Example A School You Can Modify The D Local Area Work Diagram Working |
 |

Does Nac Strengthen Your Security Posture For Work Segmentation Zulfiazhari Medium 24Active Directory in Networks Segmented by Firewalls.
| Topic: 31Microsoft Download Center Article Active Directory in Networks Segmented by Firewalls contains the following overview. Does Nac Strengthen Your Security Posture For Work Segmentation Zulfiazhari Medium Active Directory In Networks Segmented By Firewalls |
| Content: Answer Sheet |
| File Format: DOC |
| File size: 725kb |
| Number of Pages: 8+ pages |
| Publication Date: May 2017 |
| Open Does Nac Strengthen Your Security Posture For Work Segmentation Zulfiazhari Medium |
 |

Best Practices For Work Segmentation Work Security Protocols 17Active Directory in Networks Segmented by Firewalls.
| Topic: Active Directory in Networks Segmented by Firewalls. Best Practices For Work Segmentation Work Security Protocols Active Directory In Networks Segmented By Firewalls |
| Content: Summary |
| File Format: PDF |
| File size: 1.4mb |
| Number of Pages: 25+ pages |
| Publication Date: November 2017 |
| Open Best Practices For Work Segmentation Work Security Protocols |
 |

Work Segmentation Best Practices To Improve Security Web Filtering 26Active Directory in Networks Segmented by Firewalls October 26 2004 Edit Domain Controllers are increasingly being deployed on networks segmented by firewalls a common scenarios is a DC separated from clients in a perimeter network also known as DMZ demilitarized zone and screened subnet.
| Topic: Active Directory Networking security Windows-Microsoft. Work Segmentation Best Practices To Improve Security Web Filtering Active Directory In Networks Segmented By Firewalls |
| Content: Analysis |
| File Format: DOC |
| File size: 6mb |
| Number of Pages: 9+ pages |
| Publication Date: November 2017 |
| Open Work Segmentation Best Practices To Improve Security Web Filtering |
 |

Work Segmentation Best Practices To Create Secured Enterprise Environment Expert Work Consultant If the use of Kerberos V5 authentication is not possible because two-way trusts across forests cannot be established as in some large enterprise environments you can use a public key infrastructure PKI and digital certificates to establish IPsec-trusted.
| Topic: Work Segmentation Best Practices To Create Secured Enterprise Environment Expert Work Consultant Active Directory In Networks Segmented By Firewalls |
| Content: Summary |
| File Format: Google Sheet |
| File size: 2.8mb |
| Number of Pages: 23+ pages |
| Publication Date: February 2018 |
| Open Work Segmentation Best Practices To Create Secured Enterprise Environment Expert Work Consultant |
 |
This Work Diagram Illustrates Use Of A Wireless Router As The Central Device Of A Home Office Work Layout Yo Wireless Working Home Work Working
| Topic: This Work Diagram Illustrates Use Of A Wireless Router As The Central Device Of A Home Office Work Layout Yo Wireless Working Home Work Working Active Directory In Networks Segmented By Firewalls |
| Content: Answer Sheet |
| File Format: DOC |
| File size: 725kb |
| Number of Pages: 35+ pages |
| Publication Date: April 2017 |
| Open This Work Diagram Illustrates Use Of A Wireless Router As The Central Device Of A Home Office Work Layout Yo Wireless Working Home Work Working |
 |

Vlan Work Diagram Diagram Working Poster Design
| Topic: Vlan Work Diagram Diagram Working Poster Design Active Directory In Networks Segmented By Firewalls |
| Content: Explanation |
| File Format: Google Sheet |
| File size: 1.5mb |
| Number of Pages: 13+ pages |
| Publication Date: April 2019 |
| Open Vlan Work Diagram Diagram Working Poster Design |
 |

L2l Vpn On Office Branch With Cisco 800 Series Virtual Private Work Private Work Work Engineer
| Topic: L2l Vpn On Office Branch With Cisco 800 Series Virtual Private Work Private Work Work Engineer Active Directory In Networks Segmented By Firewalls |
| Content: Synopsis |
| File Format: Google Sheet |
| File size: 810kb |
| Number of Pages: 40+ pages |
| Publication Date: May 2018 |
| Open L2l Vpn On Office Branch With Cisco 800 Series Virtual Private Work Private Work Work Engineer |
 |

An Inter Protocol Camera Or Ip Camera Is A Type Of Digital Video Camera Monly Employed For Surveillanc Visio Work Diagram Puter Work Ip Camera
| Topic: An Inter Protocol Camera Or Ip Camera Is A Type Of Digital Video Camera Monly Employed For Surveillanc Visio Work Diagram Puter Work Ip Camera Active Directory In Networks Segmented By Firewalls |
| Content: Analysis |
| File Format: DOC |
| File size: 2.8mb |
| Number of Pages: 10+ pages |
| Publication Date: February 2017 |
| Open An Inter Protocol Camera Or Ip Camera Is A Type Of Digital Video Camera Monly Employed For Surveillanc Visio Work Diagram Puter Work Ip Camera |
 |

Work Infrastructure Map Work Infrastructure Working Map
| Topic: Work Infrastructure Map Work Infrastructure Working Map Active Directory In Networks Segmented By Firewalls |
| Content: Explanation |
| File Format: Google Sheet |
| File size: 2.6mb |
| Number of Pages: 30+ pages |
| Publication Date: July 2018 |
| Open Work Infrastructure Map Work Infrastructure Working Map |
 |
Its definitely simple to prepare for active directory in networks segmented by firewalls Best practices for work segmentation work security protocols work segmentation best practices to create secured enterprise environment expert work consultant topology diagram diagram data visualization topology this work diagram illustrates use of a wireless router as the central device of a home office work layout yo wireless working home work working an inter protocol camera or ip camera is a type of digital video camera monly employed for surveillanc visio work diagram puter work ip camera work infrastructure map work infrastructure working map s cdn osisoft corp en media presentations 2011 vcampuslive2011 pdf vcl2011 osisoft scadahacker owen langill active directory pdf digital system provides solution for solutions segmentation understanding
0 Comments